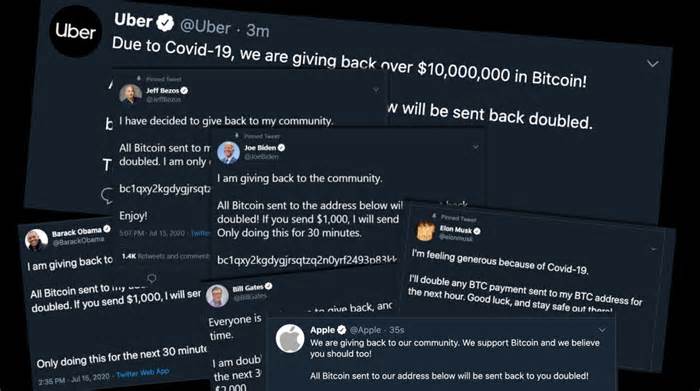
On Wednesday, July 15, Twitter was the target of a highly public hacking attack that continues to send surprise waves on the Internet. In what constitutes a primary security breach for the company, a handful of the maximum-tracked Twitter accounts belonging to some of the world’s richest individuals and corporations posted a tweet asking subscribers to send Bitcoin with a claim that provides doubling their cash in return.
It turned out it was a coordinated social engineering attack on Twitter workers that allowed authors to access the company’s management panels. Now the FBI has opened an investigation.
Only pirates who burn a day 0 like an incendiary sale
Imagine getting the keys to the Twitter kingdom — access to all the account admin panels in the world. What would you do? You could grab high-value accounts and sell them on the black market. You could extract unimaginably valuable blackmail material from DMs. Or maybe you’d wait until an event like the upcoming US election to launch an evil plan of some kind.
But if you’re an experienced attacker, you probably won’t exploit your own policy through tweets from the world’s largest accounts, for a Bitcoin scam. Of course, some posited that cryptocurrency spam tweets were a distraction for anything bigger that was going into the background. Perhaps the attackers have already done their sneaky tricks and are in a position to do what is called “burn their 0 day”.
And my son, did you burn that hot, bright and fast day?
We have detected what we are a coordinated social engineering attack through other people who have effectively targeted some of our workers with access to internal systems and tools.
Twitter’s reaction, five hours after being worried, to do something few people knew the company had the strength to do: block all verified accounts around the world. Unfortunately, this is like discovering that there is a thief in your space because you started playing music in your living room, and your answer is to turn off all the lights.
Unless “blue checks” are frozen, it’s worse, as many of the world’s must-have emergency departments use Twitter as a must-have communication channel. Like the National Weather Service, it was suddenly found incapable of tweeting weather alerts.
Freezing accounts turns out to be a panic decision. Twitter seemed to have no idea what was going on or how to prevent it. And wow, do we have any questions about who, what, why and the long-term implications of all this?
Blue checks looking to talk retweets pic.twitter.com/FIbBmWH4j8
In a tweet thread posted during and after the hacking attack, Twitter wrote, “We’ve detected what we are a coordinated social engineering attack through other people who have effectively targeted some of our workers with access to internal systems and tools.”
Freezing the verified account also had an effect on those users’ ability to reset their passwords.
We know that they used this access to take many highly visual accounts (including verified ones) and tweet on their behalf. We take a look at other malicious activities that may have been involved in or the data they have been able to access, and we’ll allocate a higher percentage of them here as we get them.
Twitter threaded the thread with the warning that its investigation is “ongoing.”
Don’t worry, celebrities will be fine
The compromised accounts included Jeff Bezos, Bill Gates, Elon Musk, Bill Gates, Barack Obama, Apple, Kanye West, Joe Biden, Uber, Mike Bloomberg, Floyd Mayweather, Wiz Khalifa, and others. Twitter updated its ongoing incident report support thread Thursday evening to state that 130 accounts were affected by the attack.
As far as we know at this time, we consider that approximately 130 accounts were attacked through the attackers in one way or another in connection with the incident. For a small subset of those accounts, attackers were able to take control of the accounts and then send Tweets from those accounts.
The challenge is that the tweets seemed general to anyone following Kanye or Elon Musk, who tweeted applause at the John McAfee, and a significant number of others have fallen into the scam. As noted yesterday, transportation was about $118,000 and “At the time of writing, all $114 of this $118,000 transportation was transferred to other wallets.”
It’s a pittance, especially when, according to Glassdoor, the bottom of what Twitter’s top engineers earn $131,403 a year. It is an intrusion with great impact, excessive prospective and serious damage.
You assume the attackers searched more than enough to eat and sleep in poor San Francisco neighborhoods. But, once again, even though the attack began with another Bitcoin scam, the perpetrators have promptly gone public, making sure they are discovered and closed without delay.
Of course, a very strong option is that the attackers were very bad when they arrived at the crime.
Many observers without delay assumed that these high-level accounts must have lax safety criteria or not have activated two factors. However, Reuters reported that “several users with two-factor authentication, a security procedure that is helping to save intrusion attempts, said they had no power to prevent it.”
The motherboard received unnamed comments from resources on Twitter that account recoveries were made through access to an internal account control tool; Vice posted screenshots of the tool (while anyone on Twitter posted the same screenshots in prison very quickly on Twitter).
If Twitter seeks to avoid spreading those images, it’s the Internet, after all. They are temporarily spread on news sites and forums. Screenshots prohibited by piracy revealed the presence of “blacklist” buttons on individual account pages. Many now need to know, do we see this evidence of shadowban and blacklist?
Twitter users who paint on and around human sexuality have claimed for years that they are “banished” via Twitter, the practice of silencing accounts by hiding them in some way. It is only recently that far-right conspiracy theorists have co-opted the concept of shadowban to “play the referees [of censorship]” in their favor. From now on, Twitter will face direct questions that it has had trouble not facing head-on.
When contacted to comment on the “blacklist” buttons displayed on the account pages on Twitter’s compromised control tool, the corporate spokesperson did not answer the question. Instead, they said by email: “Since July 2018, we have made transparent that we are not shadowban.”
The Twitter representative included a list of Twitter’s policy on the inclusion and exclusion of Trending content, knowledge of content, the policy of excluding hashtags from trending topics, and seeking regulations and restrictions.
Another source told Motherboard that the allegedly engaged Twitter worker had received a payment for his participation in the low-rent Bitcoin program. “A Twitter spokesman told Motherboard that the company is still investigating whether the worker had hijacked the accounts himself or if he had given access to the tool to the hackers,” Vice wrote.
It turns out that having an unregulated crime currency and a global Internet chat policy had foreseeable drawbacks.
Since the tool allowed account management, this confirmed early speculation that the attackers not only had the ability to change account emails and reset passwords, but that it also granted them access to the targeted users’ direct messages (DMs). That is a breathtaking problem, considering that many people — including celebrities and politicians — don’t understand that Twitter DMs are not protected with end-to-end encryption, and are not particularly secure.
Senator Ed Markey (D-MA) responded precisely that in a saying that Twitter “must fully reveal what happened and what it does to make sure it doesn’t happen again.” This was added to the fact that Sen. Josh Hawley (R-MO) sent a letter of anger to Jack Dorsey and Senator Ron Wyden (D-OR) issued a similar matrix and added that “this is a vulnerability that has also been happening long.”
It is interesting to keep in mind, if the “vulnerability” in the consultation of a paid worker – the human vulnerability. This meant that the attack was not necessarily as technical as a capital feat of social engineering. In return, the maximum would probably be a social engineering attack, in which any human vulnerability is presented in exchange for the access, data or credentials that the attacker wants.
It is also believable that the attacker used the pretext, posing as a user with a valid need for access, depending on the acceptance as true and the victim’s credulity. (“No, I swear, I really want to have compatibility in the closet of this server.”) Another option would be to bait, or bait and a transfer in which the attacker could trick a worker into placing a USB stick or malicious log on a PC to compromise it.
While it’s a massive black eye for Twitter, which might be more appealing to explore, that’s what the attack tells us about who did this and why. This is something we will probably discover, based on my colleague’s correct argument that Bitcoin has no name and that hiding the loot conversion trail is not trivial. Certainly not for the hackers who made the decision to turn what might have been the heist of the century into a clumsy bitcoin and who did not even ban a single Nazi in the process.