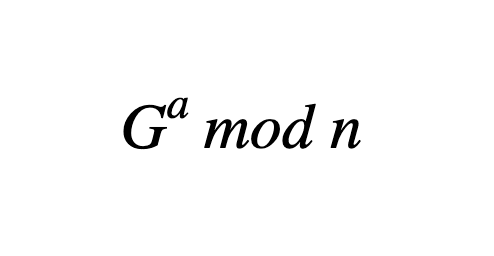I’m going to communicate about Bitcoin’s addresses and security keys, called public key cryptography, which includes SHA256, random number turbines (RNG), hash functions, and virtual elliptic curve signatures (ECDSA). , feel free to touch me through DM. I’m a mathematician by education and I love it. If you discover that you have a new interest in cryptography as a hobthrough, many other people create cryptographic algorithms for fun, and your network can be useful for your journey.
I promise you just want some fundamental algebra for this, as well as an undeniable understanding of exponential functions. If you’re familiar with modular arithmetic, this is wonderful. Otherwise, it’s no big deal.
Cryptography has been around for thousands of years and currently has a very strong network of professionals and amateurs. The generation has arrived a long time ago and its existing iterations allow for an online security that we barely need to think about.
Let’s start with the concept of public key cryptography, especially in the context of Bitcoin. At the maximum fundamental level, PKC reaches your personal keys and the public keys generated from them. PKC uses so-called “cheat functions” that are simple to solve (simple to generate a public key from a personal key), but to the maximum to invert-congs (find a personal key from a public key). This is due to the use of modular arithmetic, exponential functions and giant primes.
Your personal bitcoin keys are probably words, but they can also be a very large number. To be precise, when we start with encryption, your personal keys will be changed to a giant number or binary string (series of ones and zeros) regardless of their initial shape How nice!That’s why other people say that your personal keys “represent a very, very giant number” and are the explanation for your security. While this is technically true in a deterministic/algorithmic sense, it’s not necessarily obvious why.
The generation of personal keys is another attractive facet. Hardware and custody wallets do it for you, and they may or may not tell you exactly how they do it (open source software or closed software). opt for a wallet. The other option is to create your own from scratch. You can toss a smart d, toss a coin, or use some other similar method. There are also online random number turbines that have been tested and qualified through the professional cryptography community. RNG uses the existing time as a generator to create a small initial difference that, after enough iterations, creates an absolutely unique number. Choose an online RNG at your own risk. Even though the RNG itself is smart, there would possibly be malware on the site.
Then we have our secret words. Let’s see what happens next.
This is a very undeniable form of our cheating function. “G to the a mod n” represents our final public key (mod is short for modular arithmetic, which restricts our reaction to a safe limit of numbers, as opposed to each and every number unique to herbs). But, even if you know Gyn, there is no undeniable way to locate, which represents your personal key. Calculating G to mod n is undeniable, but there is no going back, thanks to the discrete register problem. N is usually a prime because they are infactorials through the definition. Also, if you are interested in the relative complexity of functions/problems, feel free to take a look at the temporal complexity of the algorithm.
Let’s go a little further and look graphically for a more concrete understanding.
The red line is our curve, and it is the express line that is used through Bitcoin ECDSA. G is the starting point, our “generator”, if you will. Next, let’s “add” G to itself (even though it’s not an addition in the same old sense of the word: those nutty mathematicians love to redefine things. Don’t even get me started with topology!). In this case, adding means that we will take the tangent of this point. Where this tangent line intersects, the curve will be our next point. We will remove the tangent and locate a new point. In practice (on a computer), this is done thousands or even millions of times. The end result is that even though you know where I started, you don’t know how many times I “added” G to himself to get to the end point. How many times have we made the addition is your personal key (your personal number). Again, this is easy to determine given a prospective answer, but almost to “brutal force”. here!
So we have our first deterministic encoding (an input gives you an answer) of data, but it’s not in a giant format (at the moment, it’s just an ordered pair (x, y). We now have a public key, derived from a Draft, backing up this data and it.
We do this through SHA 256, which stands for Secure Hashing Algorithm. A hash rule set is an express set of steps that are implemented in information, resulting in an encrypted set of fixed-duration data, regardless of the lifetime of the input. .
Yes, this circle of relatives of the alpassritmos evolved through the United States National Security Agency (NSA), but do not worry, the past looks of the implemented sciences, adding mathematics, lies in the fact that discovery and wisdom are independent of who developed them. That is why we have evidence. If the evidence is “solid”, then it stands firm and cannot be “hacked” or overlooked. The SHA2 circle of relatives is not an unusual wisdom. You can go online and take a look at the code, and if you want, use SHA256 yourself to encrypt some things. You will find that a very small replacement at the input will have a dramatic output in response. Chaos theory is beautiful. But anyway.
Since many other people have saved billions of dollars with SHA256, they have also spent a lot of cash to verify their safety. People communicate about quantum computing as a prospective way to break this encryption. However, if quantum computing has become feasible, there would be much more money to be stolen by hacking the five largest banks in the world. I’m sure Bitcoin is way down the list because, once hacked, its price would likely be significantly minimized. That said, if SHA256 becomes less secure in the future, we can still update Bitcoin’s encryption methods. Programmable cash!
SHA256 is similar to ECDSA in that it is simple to determine an answer, but very difficult to force brutally: look for each answer until you find the right one. SHA256 is so named because it creates a 256-bit string, a string of 256 zeros, and ones. This provides an absurdly higher number of imaginable combinations, rather than the number of atoms in the observable universe.
Image source
We’ll use another hash back to get a smaller output, allowing for a shorter final address. This hash serves as it is called RIPEMD-160. Once we have this result, we will convert it to what is called Base58, which is just a more human-readable form, omits the number 0 (0) and the capital letter O (o), so they are not arrays as well as omitting the uppercase letter I (i), so that it is not with the number one (1) or the lowercase letter l (L) It omits the digit 0 (0) and the uppercase letter Or (o) Array so are not Array as well as omitting the capital letter I (i), so it is not with the number one (1) or the decreasing capital digit l (L).
And now we have a public confrontation that can be demonstrated (in a formal and mathematical sense) created from a single personal confrontation. Even though the other seven billion people in the world create a new bitcoin public key every day for a thousand years, the odds are such that the probability of creating the same two times is almost zero.
All this is a total process, creating and verifying keys, hence our average lock time of ten minutes. Ten minutes for a mathematically guaranteed final agreement is everything.
This is a guest post by Nameless. The reviews expressed are entirely yours and do not necessarily reflect those of BTC Inc. or Bitcoin Magazine.